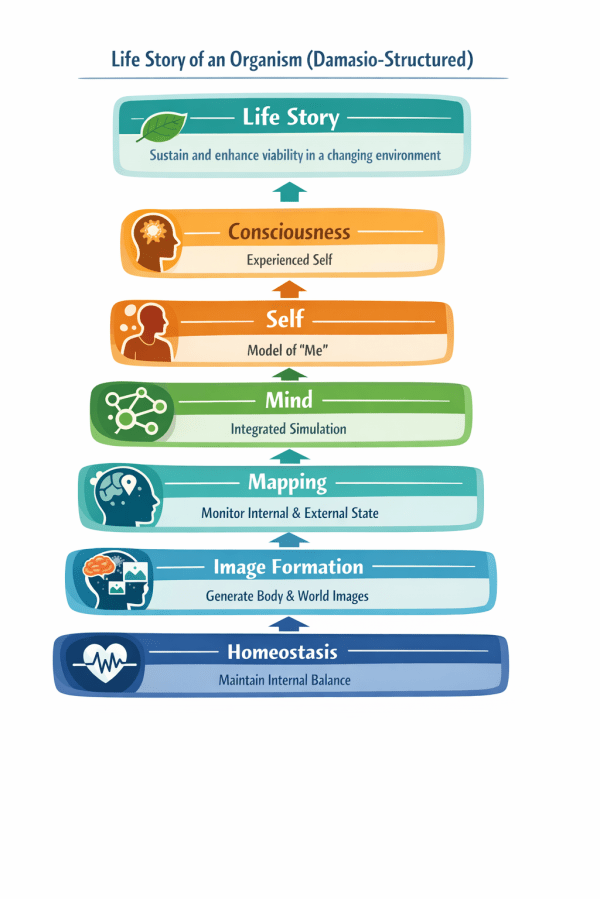
As a living organism, / I need to sustain and enhance my viability in a changing environment, / so that I can continue existing and flourishing…
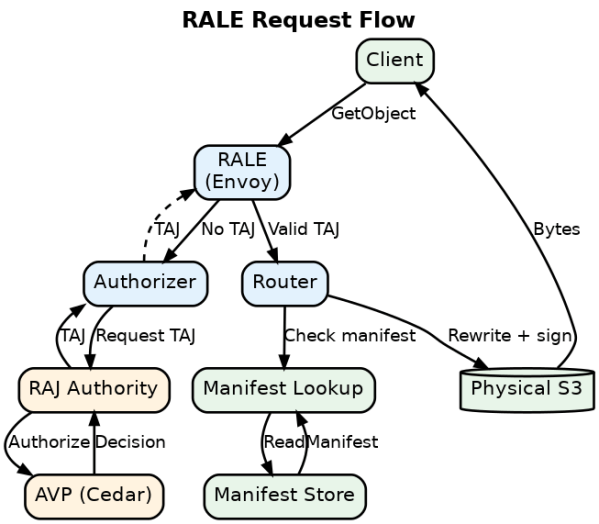
RALE: RAJ-Authorizing Logical Endpoint
Clients shouldn't know bucket names, regions, or AWS accounts Access should be fine-grained (specific packages, not entire buckets) Authorization should be efficient (not re-evaluated per file) Data locations should change without breaking client code Traditional S3 approaches fail...
The Boy Who Ate The Menu (RAJ/TAJ as Software-Defined Addressing for Universal Storage Locators)
Explain how SDA is like being able to “eat the menu;” as a Roald Dahl story.
IAM as Maharaja: How RAJ Redeems the Original Sin of Cloud Authorization
Schmitt: / And sovereignty appears only where it belongs: / at the boundary of legitimacy, not inside every action…
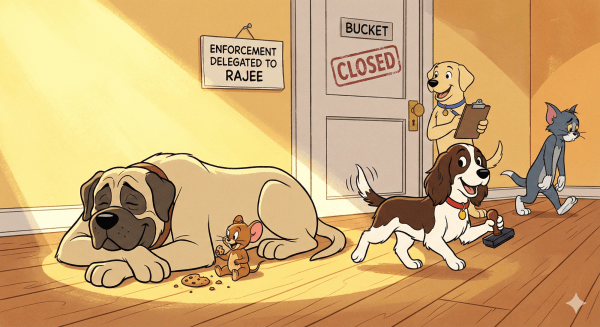
RAJEE vs IAM: The Petty Life of Secrets
When judgment retires upstream, enforcement gets simple, guards get happy, and Jerry gets the cookie
Simple Two-Person Euchre
Head-to-head Euchre: burn four cards, race to 10 points, and dealer always scores for turning a Jack.
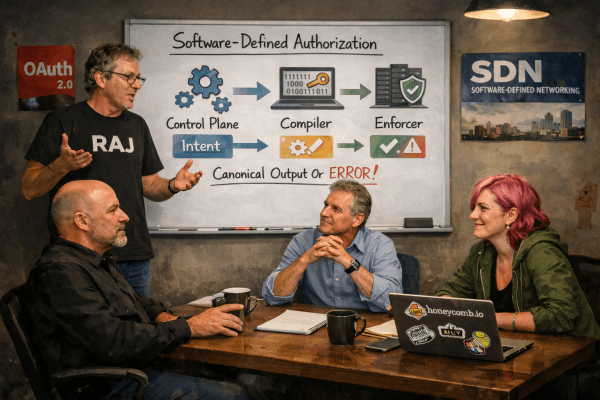
SDA: Strictly Disciplining Authorization
At no point does the system accept, contain, transmit, or act upon a non-canonical representation.
Crowning RAJ: How Resource Access JWTs Refactor Authorization Joyfully
“I’m not here to propose a new access-control system. I’m here to remove three.”
Multimodal Data Management: The Inevitable Category?
“What’s missing is the thing we had for structured data. But for… all of this.”
Diaphorum 1.5: Primitive Forms of Argument
MSRP: Replace spacetime + Markov dynamics with something simpler that still predicts everything.





You must be logged in to post a comment.